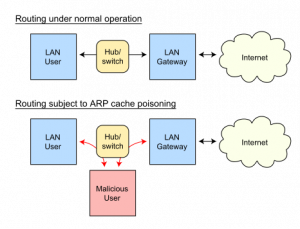
 ARP spoofing,, is a technique used to attack a local-area network (LAN). ARP spoofing may allow an attacker to intercept data frames on a LAN, modify the traffic, or stop the traffic altogether. The attack can only be used on networks that make use of the Address Resolution Protocol (ARP) and not another method of address resolution.
ARP spoofing,, is a technique used to attack a local-area network (LAN). ARP spoofing may allow an attacker to intercept data frames on a LAN, modify the traffic, or stop the traffic altogether. The attack can only be used on networks that make use of the Address Resolution Protocol (ARP) and not another method of address resolution.
How to Defense
An open source solution is ArpON “ARP handler inspection”. It is a portable handler daemon that make ARP protocol secure in order to avoid the Man In The Middle (MITM) attack through ARP Spoofing, ARP Cache Poisoning, ARP Poison Routing (APR) attacks. It blocks also the derived attacks by it, which Sniffing, Hijacking, Injection, Filtering & co attacks for more complex derived attacks, as: DNS Spoofing, WEB Spoofing, Session Hijacking and SSL/TLS Hijacking & co attacks.
Other defenses against ARP spoofing generally rely on some form of certification or cross-checking of ARP responses. Uncertified ARP responses are blocked. These techniques may be integrated with the DHCP server so that both dynamic and static IP addresses are certified. This capability may be implemented in individual hosts or may be integrated into Ethernet switches or other network equipment.
Some switch vendors have devised a defense against this form of attack that imposes very strict control over what ARP packets are allowed into the network. The feature is known as ARP Security or Dynamic ARP Inspection.
The simplest form of certifiation is use of static, read-only entries for critical services in the ARP cache of a host. This only prevents simple attacks and does not scale on a large network, since the mapping has to be set for each pair of machines resulting in (n*n) ARP caches that have to be configured.
The existence of multiple IP addresses associated with a single MAC address may indicate an ARP spoof attack, although there are legitimate uses of such a configuration.
In a more passive approach a device listens for ARP replies on a network, and sends a notification via email when an ARP entry changes.
Also, using a VPN or encryption to prevent people from sniffing your traffic in a hostile environment. you can also make a static arp entry in your windows machine if you know the right MAC address of the router with:
arp -s <gw_ip> <gw_mac> at my environment i have a software called arpwatch on the firewall to see if someone play tricks on my network.
you can also consider implementing somekind of NAC(Network Access Control) at your Switches to prevent unauthorized clients on your network.
Defense Tools
- ArpON – ARP handler inspection
- ARPDefender appliance
- Arpwatch
- XArp
- anti-arpspoof
- AntiARP
Source: Many Network Security articles and wikipedia

Geez, that’s unebeliavble. Kudos and such.