 What You Should Know About Unified Threat Management (UTM)
What You Should Know About Unified Threat Management (UTM)
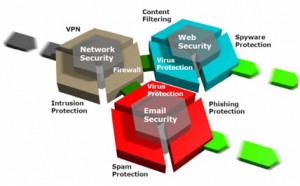
Unified Threat Management eliminates the need for machine to machine protection. It is the combination of multiple security features integrated into one single hardware platform. Therefore offering layers of security features within a corporations network.
The Machines UTM Machine, is what provides multiple solutions to an entire network of machines. It works off the assumption that blended threats cannot be abated under one solution alone. Even with the use of multiple solutions there seems left a hole within the security of the network. When there is the use of multiple different solutions there seems a confusion as well as the need for updates and monitoring of several different brands of security measures which lead to problems within an organization.
With the introduction of Unified Threat Management in 2004, this idea was taken and turned into one system solution for businesses on the small to medium level. The idea of this solution was to take the need for multiple brands of solutions and combine it into a multilayer solution for the security needs of an organization.
In order for this to work, the Unified Threat Management system, must consist of its own operating system, therefore decreasing the need for human intervention. This means the system, therefore should possess the capacity to perform gateway anti virus, network fire walling, and network intrusion detection and prevention.
Although the system would have such capabilities, the company would not have to utilize each of the functions, however the Machines UTM Machine should contain the ability to function at those capacities when needed. Some of the other functions that it should possess are such features such as policy management and security management according to each user or group. Today, many of them have such features such as a Virtual Private Network (VPN), anti-spam, and in some cases Load Balancing, and Multi-Link Module.
Through the integration of a Unified Threat Management system, it helps to manage security of a network, with only having to worry about one device and not several individual solutions. Additionally, there is only the need to set up one source for security, which ends up as an easier and more cost effective way to manage all aspects of a businesses security. The Machines UTM Machine functions as a single console, with the ability to provide all relevant information on network traffic patterns as well as the user patterns within the network.
Many of them that you will find, focus only on IP address reporting and controls, while allowing the user to stay invisible. In some cases this may allow for security threats especially from inside the organization. This can be overcome by releasing the traditional approach of TCP/IP protocol stacks, which only allows recognition of the IP of a machine on a network. Further security is obtained through an identity based UTM, which allows the system to identify each of the users within the network according to access policies and not only according to the IP address of a machine.
This furthers security within the network internally as well as externally as well. Each users or groups are given access rights and are in accordance to the business needs of that group or user. The UTM can allow access based on privileges that are set rather than IP alone. UTM has the ability to provide excellent security as long as configurations are followed and extra measures are taken in order to protect the network internally as well as externally.
